Securely connecting your IT with your OT using a demilitarized zone (DMZ).
The need for security
In recent years, the digitalization was quickly moving forward and is setting in every aspect of our surrounding. Especially with the Internet of Things (IoT) we developed technology that enabled us to interconnect more and more devices.
This development took also place in the industry where nowadays data to every time and location can be gathered and used by connecting computer, servers, but also industrial machines and sensors to a network.
This is also known under the terms Industry 4.0 and Industrial Internet of Things (IIoT).
However, in addition to the advantages, digitization also accommodates different risks. Cybersecurity is a key topic and especially in the industry, a successful attack can have an enormous damage. A stop of production for one day may have a huge impact on not only a single company, but also the whole supply chain network.
Especially ransomware is a prominent example of current cyberattacks on companies. It is a type of malware that is encrypting data to lock it for the user. Within the last years there were several cases reported in the news, in which big companies became victims to ransomware attacks (e. g. Garmin, Pilz, Accenture, etc.)
"Die Wucht, mit der Ransomware-Angriffe unsere Wirtschaft erschüttern, ist besorgniserregend und trifft Unternehmen aller Branchen und Größen."
"The force with which ransomware attacks are shaking our economy is worrying and affects companies of all industries and sizes."
- Achim Berg, President Bitkom -
Studies from McKinsey show, that implementing new technologies can be risky for most manufacturing companies and cybersecurity should therefore be integrated into core processes of a company.
Bitkom is reporting the annual damage to companies in the German economy caused by cyberattacks to be over 220 billion Euros.
But how can a manufacturing company protect themselves from cyberattacks?
Prevention of cyberattacks through Information Security
In a manufacturing company there are two different technology systems: Information Technology (IT) and Operation Technology (OT). If you are interested in more background information to IT and OT, we recommend our article: The story of IT and OT - why two systems are better than one
Both IT as well as OT are systems that are open by default, due to historical reasons:
- ARPANET, the predecessor of the internet, was developed by American universities to connect and share information among trusted individuals such as professors researching on the same topic. This is the reason why up to this day the internet is not designed to be secure but to gain access and to share information.
- The same goes for automation networks: the first connection between PLCs were inside of a factory hall or maybe across a plant including only trusted participants.
This is the reason why a manufacturing company needs to focus on two concepts to protect itself from cyberattacks:
- IT-Security, which describes the security of office equipment such as computers and servers (IT) and
- Industrial Security, which is focusing on the security of production machines and systems (OT)
Most of the currently used IT Systems are already connected to the internet which is why they normally have protective countermeasures in place to secure from security risks.
On the other hand, the OT environment, such as the shopfloor, is just starting to increasingly connect all the OT devices. In the context of IIoT it is a growing topic and with that Industrial Security related issues are getting ever more important.
But what is Industrial Security about? What are the goals and common attack vectors?
Attack vectors & common countermeasures
Lets start with the goals of Industrial Security. One well-established framework in Information Security is the CIA triad:
C: stands for Confidentiality. For machinery this means, e.g., to protect confidential process parameters from the competition.
I: stands for Integrity. For machinery this means, e.g., to prevent data manipulation from an unsatisfied employee.
A: stands for Availability. For machinery this means to ensure the continuous availability of all systems and machines without any downtimes caused by, e.g., ransomware attacks or misconfiguration.
Unfortunately, OT systems such as the PLCs are often configured open by default. They need to be adjusted by closely following the manufacturers instruction to properly secure the OT systems. But security is not always the first priority in implementation projects ("Let's just do it later") which can leave various attack vectors open. Common mistakes are:
- Default passwords not changed
- Ports and unnecessary services not disabled
- No updates for known vulnerabilities
- Not leveraging the full capabilities of Industrial Protocols, e.g., encryption and signing using certificates in OPC/UA
A full list of attack vectors and countermeasures can be found not only at PLC manufacturers websites, but also at the "Bundesamt für Sicherheit in der Informationstechnik (BSI)" (German Federal Office for Information Security) and in the "IT-Grundschutzkatalog", Chapter ICS.
With the United Manufacturing Hub, we often experience that companies are either not considering industrial security as a major issue in their facilities or are overcautious and with that unintentionally blocking digitalization projects.
An example for companies that are not cautious about security is that we saw production machines, worth worth hundreds of thousands of Euros, still running on Windows 7 (which support ended January 2020), XP or even older. Those machines were directly connected to the internet only protected with a firewall.
The overcautious companies on the other hand are often using the airgap network security measure which is not connecting the machines to the internet at all. Nevertheless, that narrows their opportunities when it comes to digital transformation processes.
Nevertheless, there is a method that is very well suited for IIoT. It is the creation of a Demilitarized Zone (DMZ) that enables all the benefits of modern digital solutions and protect valuable assets at the same time.
DMZ
There are several industry-wide standards, established by leading companies and organizations, that recommend a segmentation of the business network system from the plant networks.
Cisco, Rockwell Automation, VDMA, and more, are recommending to create a Demilitarized Zone (DMZ), sometimes also referred to as a perimeter network. It is a common approach used in general IT-network security but is still in an early adoption phase for IIoT devices.
The reason behind using such and DMZ is, that IIoT devices cannot be fully protected by a single technology. Therefore, it is recommended to use a defense-in-depth security approach to secure each asset. The approach is able to protect from multiple threats which makes it more suitable than a single technology approach, for example using only a firewall.
The following picture is showing a simplified example from a general IT perspective, in order to better understand the principle.
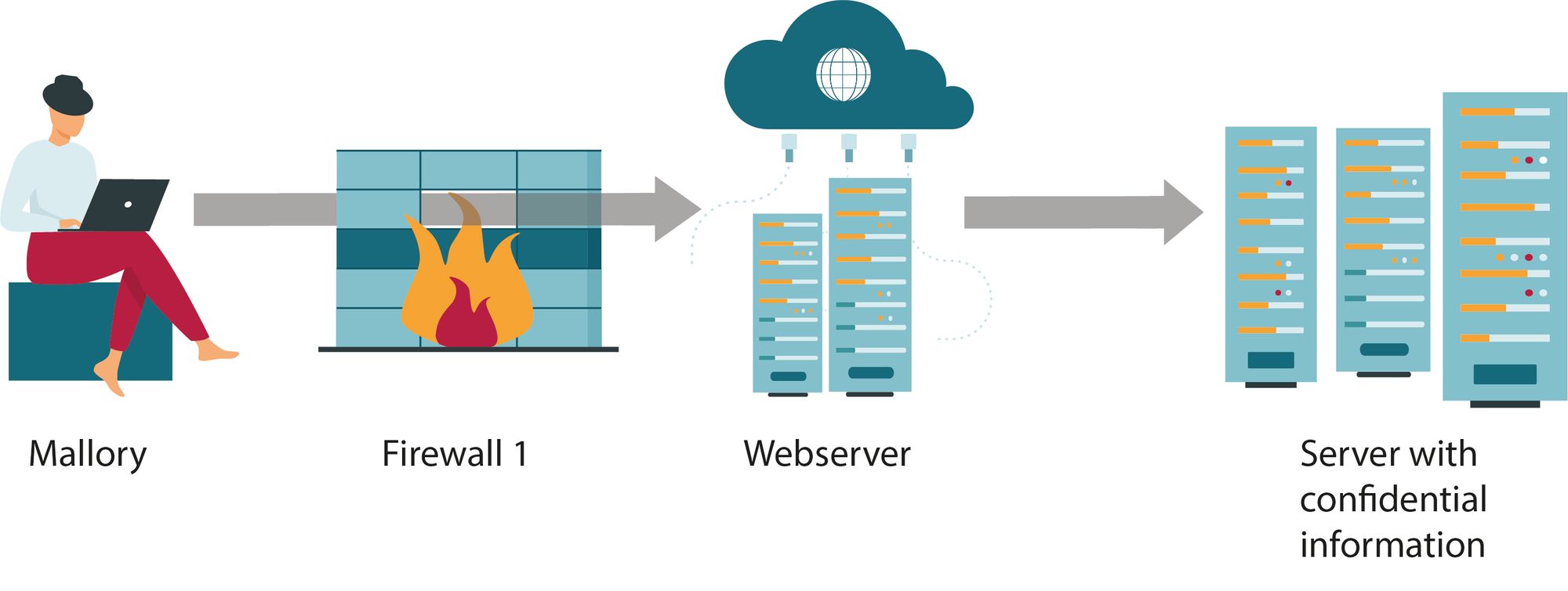
The simple example is that all IT devices such as computers, servers, etc. are connected in one network which is called Local Area Network (LAN). The LAN is then protected by a firewall from the Wide Area Network (WAN), which is also called internet.
Within the LAN there is a webserver running that hosts a website. A firewall is configured to enable access from the internet to visit the website.
With the assumption that there is one vulnerability in the webserver, a hacker (Mallory) is able to access the webserver and from there enter the entire LAN including every sensitive device such as file storages.
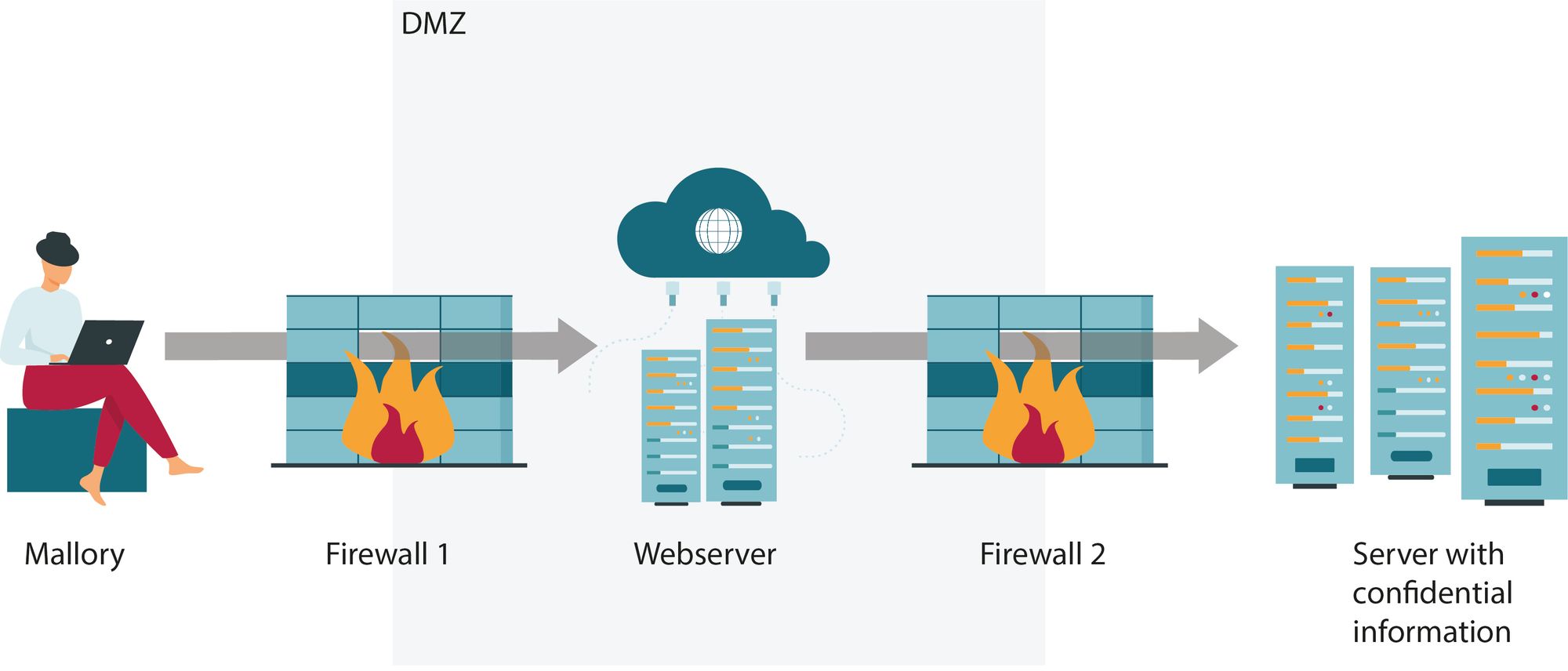
By establishing a DMZ we are creating a buffer zone between the internet and the LAN. The webserver can now be placed in the DMZ zone while critical software components remain in the LAN.
Should a hacker be able to access the webserver, there is now an additional full-fledged firewall which reduces the probability of a single point of failure with a full network breach as a result.
How DMZ works in the United Manufacturing Hub
The same principle from the example can be applied to the OT environment. The companies IT network is usually connected to the internet with a firewall in place. However, there are cybersecurity risks, such as phishing mails, related to the IT network which makes it a threat for the OT network. Therefore, the OT can be protected by using a DMZ.
Sometimes manufacturing companies already use a separate OT network, which connects various PlCs with each other. Nevertheless, especially in discrete manufacturing, machines are not connected at all yet. The DMZ principle can also be applied in both of those cases which is why we use OT network and PLCs synonymously in the following.
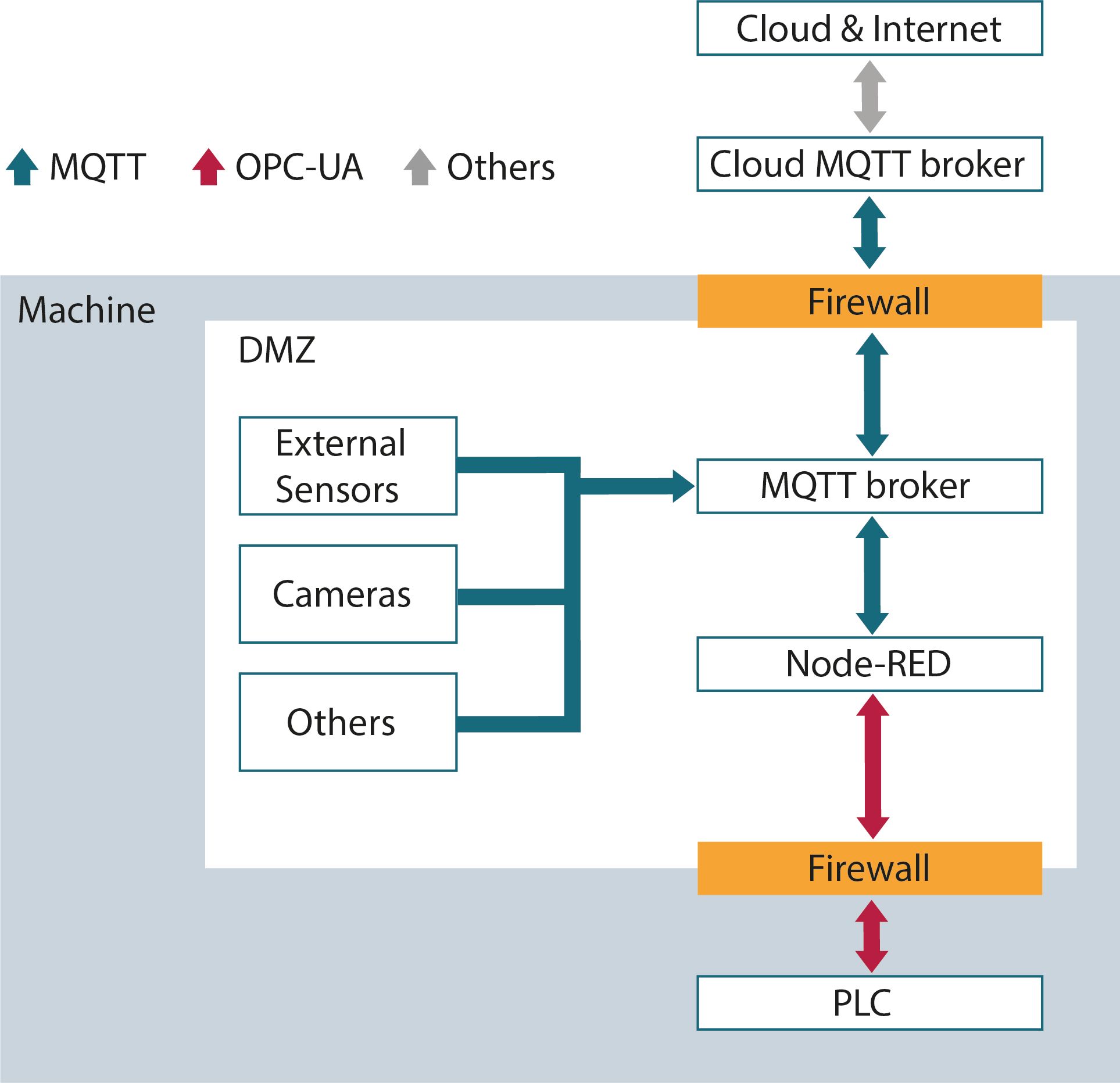
With the United Manufacturing Hub we recommend to connect the PLC directly to the DMZ firewall. Within the DMZ there is the Factorycube-edge stack running which contains Node-RED and a MQTT broker.
Node-RED itself is protected by a password and is the only software allowed to access the PLC through the firewall (and with that only the relevant ports, e.g. OPC/UA). It sends the retrieved data to the MQTT broker, from where a MQTT bridge is going to the MQTT broker of the factorycube-server stack (for example in a cloud environment).
This structure minimizes the attack surface for potential hacks from the IT network and also creates multiple security layers that prohibit an easy access to the PLC (ignoring physical access attacks and vulnerabilities in the firewalls).
The steps to force access to the PLC from outside would be:
- leveraging a security vulnerability of the software running in the DMZ, e.g., insecure update process or injection using MQTT messages
- get into Node-RED, e.g., brute-forcing the password
- leverage a security vulnerability in the OPC/UA protocol to gain access
With the DMZ approach a manufacturing company can protect even a misconfigured and insecure PLC from outside attacks. However, it does not protect from every threat for example against phishing attacks. An employee, having a virus on its computer and connecting physically with the PLC to reprogram it, can still transfer malware and with that allow access.
Nevertheless, this approach will hopefully make ransomware economically unviable.
If you are interested in gaining a deeper understanding of our concept, please read our documentation about the architecture of the United Manufacturing Hub.
Conclusion
Using the DMZ is good approach to split up the companies IT-architecture into different networks and increase the cybersecurity in the result. Creating several DMZ follows a defense-in depth security approach and builds a highly flexible but also highly secure architecture.
Actively managing this set up will help to reduce the attack surfaces of the company and still enable the advantages of new Industry 4.0 technologies at the same time.
About the authors:
Christian Proch, Co-Founder and CFO/CMO of the United Manufacturing Hub. Tech enthusiast that did a MBA with the focus on innovation and now following digital trends.
Jeremy Theocharis, Co-Founder and CTO of the United Manufacturing Hub. IT-nerd that studied Mechanical Engineering and Business Administration at RWTH Aachen and learned programming with 14.





